By leveraging Microsoft Intune, Devicie can accelerate and simplify your Essential Eight program. Our advanced platform streamlines delivery and ongoing management of endpoint devices, ensuring seamless compliance.
Devicie enables the rapid deployment of a secure and productive Intune instance, tailored to the specific needs of your customers' organizations.
Devicie's Essential Eight templates and configuration matrices support a staggered approach to compliance, enabling you to achieve maturity level 1 in one mitigation strategy while progressing to maturity level 2 in others. This approach allows for the independent implementation of each level, providing flexibility and enhanced change management control, without the need for a blanket "Level 2 for all controls" method.
The table below outlines the areas where Devicie contributes across each maturity level, indicating what we achieve and what responsibilities remain with partners or clients.
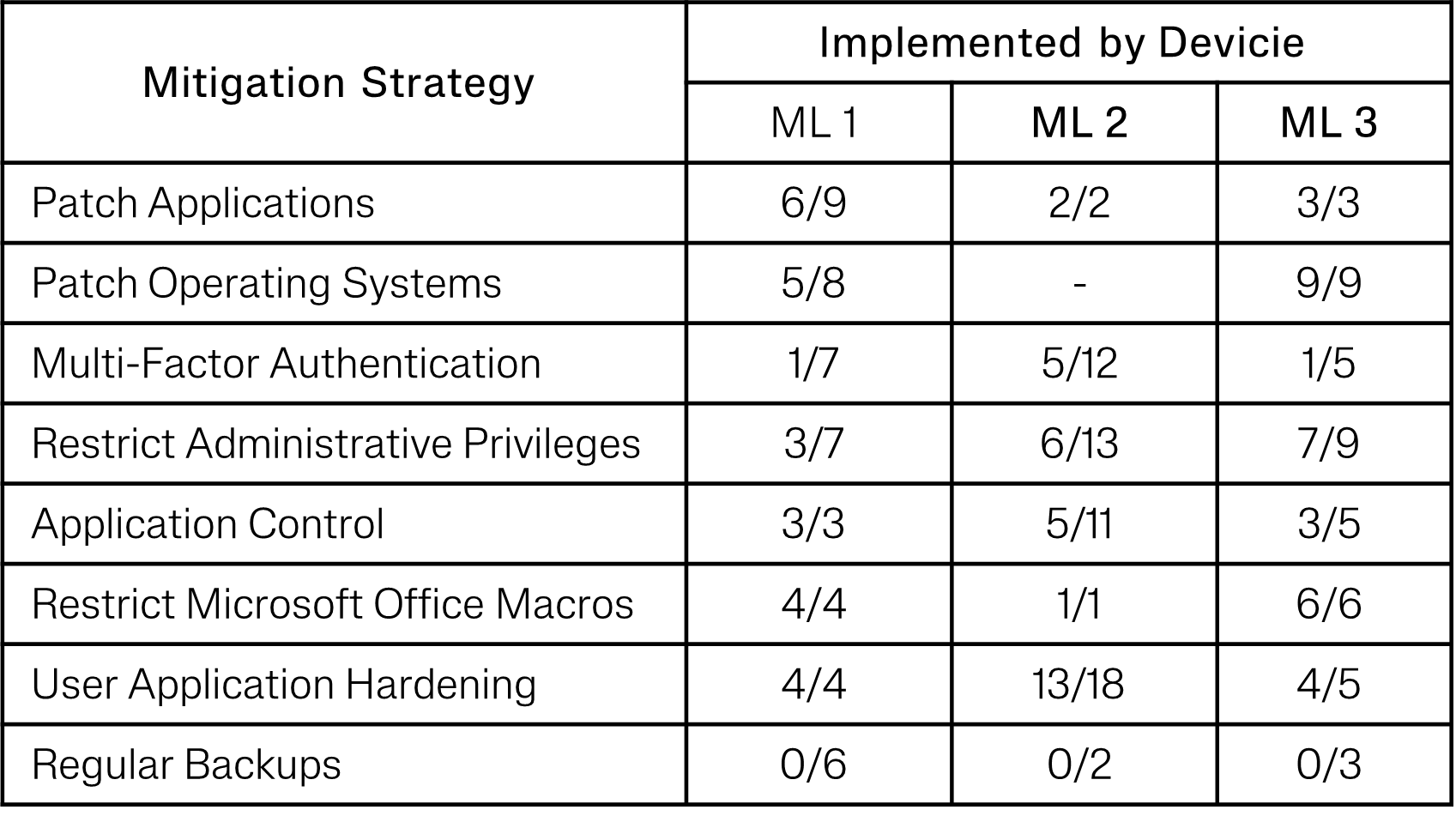
Note: The Essential Eight guidelines require that each maturity level be fully achieved in sequential order. This means that even if Devicie implements 100% of Level 2 controls, missing Level 1 items must be completed by the partner to reach full maturity status. For example, achieving Patch Applications Level 2 requires that Level 1 controls be implemented first.
Devicie provides a detailed breakdown of the 150+ controls, specifying which ones we implement and offering general guidance for partners or clients to address the remaining components. We manage each required control to ensure that every assigned device adheres to the necessary standards. Devicie also efficiently handles continuous automated maintenance, monitoring, and remediation within Intune. If there are changes to the Essential Eight requirements, Devicie updates its policies accordingly, with new policies automatically deployed to applicable environments, giving organizations the flexibility to determine when to assign them to production devices.
References:
Essential Eight Assessment Process Guide | Cyber.gov.au
Essential Eight Explained | Cyber.gov.au
Essential Eight Maturity Model FAQ | Cyber.gov.au
ACSC Essential Eight - Essential Eight | Microsoft Learn
Essential 8 | M365 Maps